|
DEFINE VARIABLE selection AS INTEGER NO-UNDO FORMAT "9".
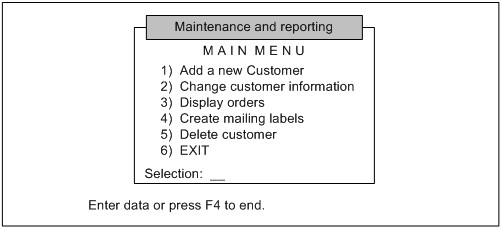
RUN _prostar.p. REPEAT: FORM SKIP(2) " M A I N M E N U" SKIP(1) " 1) Add a new customer" SKIP(1) " 2) Change customer Information" SKIP(1) " 3) Display orders" SKIP(1) " 4) Create mailing labels" SKIP(1) " 5) Delete a customer" SKIP(1) " 6) EXIT" WITH CENTERED TITLE "Maintenance and Reporting". UPDATE SKIP(2) SPACE(1) selection AUTO-RETURN WITH SIDE LABELS. HIDE. IF selection EQ 1 THEN RUN i-adcust.p. ELSE IF selection EQ 2 THEN RUN i-chcust.p. ELSE IF selection EQ 3 THEN RUN i-itlist.p. ELSE IF selection EQ 4 THEN RUN i-rept6.p. ELSE IF selection EQ 5 THEN RUN i-delcus.p. ELSE IF selection EQ 6 THEN QUIT. ELSE MESSAGE "Incorrect selection - please try again". END. |
|
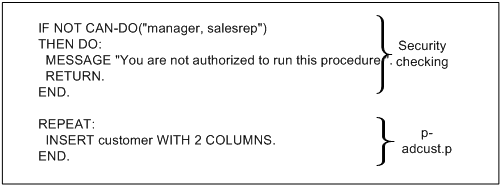
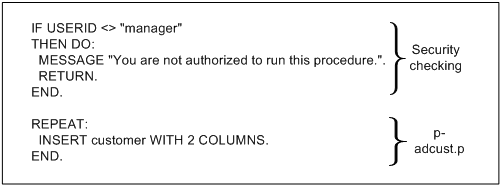
REPEAT:
INSERT Customer WITH 2 COLUMNS. END. |
|
Value
|
Meaning
|
|
*
|
All users are allowed access
|
|
user
|
This user has access
|
|
!user
|
This user does not have access
|
|
string*
|
Users whose IDs begin with string have access
|
|
!string*
|
Users whose IDs begin with string do not have access
|
|
This pattern...
|
Matches...
|
|
The blank user name in the blank domain
|
|
|
*
|
All user IDs
|
|
mark@acme.com
|
The "mark" user name in the "acme.com" domain
|
|
mark
|
The "mark" user name in the blank domain
|
|
mark*
|
All user names that begin with "mark" in the blank domain
|
|
*jones
|
All user names that end with "jones" in the blank domain
|
|
db*user
|
All user names that begin with "db" and end with "user" in the blank domain
|
|
@acme
|
The blank user name in the "acme" domain
|
|
*@acme
|
All user names in the "acme" domain
|
|
@
|
The blank user name in the blank domain
|
|
mark@*
|
The "mark" user name in any domain
|
|
*@*
|
Any user name in any domain
|
|
mark*@acme.*
|
Any user name that begins with "mark" in any domain that begins with "acme."
|
|
*@*.admins
|
Any user name in any domain that ends with ".admins"
|
|
IF CAN-DO(hCP:ROLES, "Admin") THEN ...
|