|
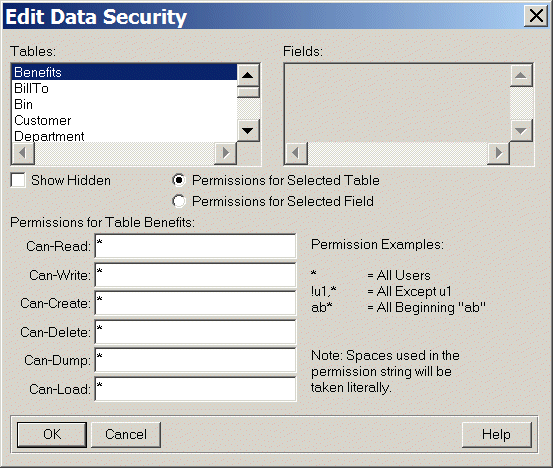
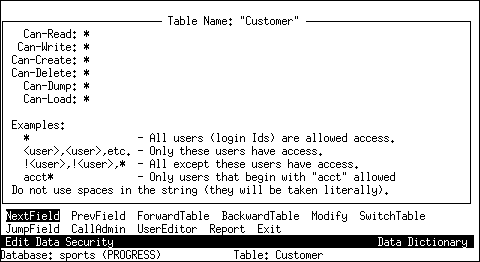
Permission
|
Description
|
|
Can-Read
|
Specifies the users who have permission to read a table or field.
|
|
Can-Write1
|
Specifies the users who can write to a table or field or update records.
|
|
Can-Create
|
Specifies the users who can create new records. The user with Can-Create privileges automatically has Can-Write privileges.
|
|
Can-Delete
|
Specifies the users who can delete records from a table.
|
|
Can-Dump
|
Specifies the users who can bypass dump trigger security by using DISABLE TRIGGER.
|
|
Can-Load
|
Specifies the users who can bypass load trigger security by using DISABLE TRIGGER.
|
|
Expression
|
Meaning
|
|
[,]<blank>,...
|
The blank user ID has access.
|
|
*
|
All user IDs have access.
|
|
mark
|
The user ID "mark" has access.
|
|
!mark
|
The user ID "mark" does not have access.
Note: The ! permission negation is useful only when the permission list ends with ",*"
|
|
,!mark,*
|
The blank user ID and the user ID "mark" do not have access.
|
|
mark*
|
All user IDs that begin with "mark" have access.
|
|
*jones
|
All user IDs that end with "jones" have access.
|
|
db*user
|
All user IDs that begin with "db" and end with "user" have access.
|
|
This expression . . .
|
Permits access to tables and fields from . . .
|
|
The blank user name in the blank domain
|
|
|
*
|
All user ID's
|
|
mark@acme.com
|
The "mark" user name in the "acme.com" domain
|
|
mark
|
The "mark" user name in the blank domain
|
|
mark*
|
All user names that begin with "mark" in the blank domain
|
|
*jones
|
All user names that end with "jones" in the blank domain
|
|
db*user
|
All user names that begin with "db" and end with "user" in the blank domain
|
|
@acme
|
The blank user name in the "acme" domain
|
|
*@acme
|
All user names in the "acme" domain
|
|
@
|
The blank user name in the blank domain
|
|
mark@*
|
The "mark" user name in any domain
|
|
*@*
|
Any user name in any domain
|
|
mark*@acme.*
|
Any user name that begins with "mark" in any domain that begins with "acme."
|
|
*@*.admins
|
Any user name in any domain that ends with ".admins"
|